| 342 | IETE TECHNICAL REVIEW, Vol 23, No 6, 2006 |

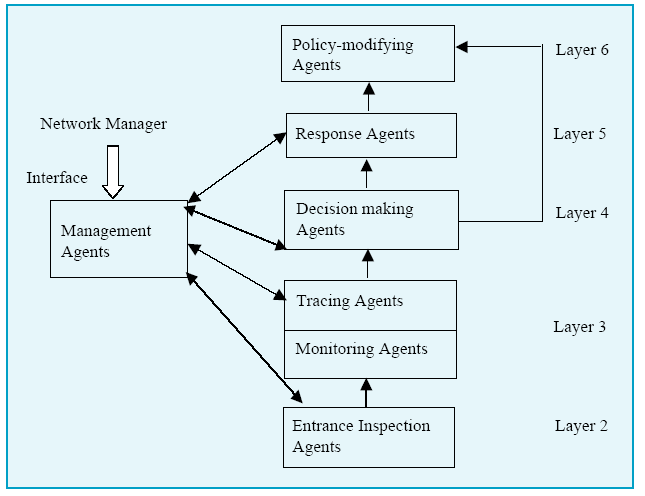
Fig 1 Multilayer IDS using Mobile Agents
Once the anomaly has been detected the attack type and attacker is determined. This is done by getting the detailed attack information from a set of identification rules, which have been precomputed for known attacks. 6. SECURING EXISTING ROUTING PROTOCOLS Traditional routing protocols have to be made secured because they were not fundamentally designed to be secure [10, 26]. Table 2 shows different attacks suffered by various routing protocols. Some of the modifications to secure existing routing protocols for MANET are discussed below. 6.1. Securing AODV Protocol The AODV Protocol suffers from Black Hole problem, where an attacker node routes all the packets to itself as being the destination and later discard all the packets. One solution [10] is allowing only the destination nodes to reply a route request and restricting the intermediate nodes for the purpose. Another solution is to check the existence of the route from intermediate node to the destination by using one more route to the intermediate node that replays the packet. |
Alampalayam et. al. propose [27] a Routing Attack Security Model (RASM) for securing MANETs against, Black Holes. This model has three modules: |
|||||||||||||||||||||