| OMAR FAROOQ et al : TAMPER-PROOFING OF DIGITAL IMAGES |
351 |

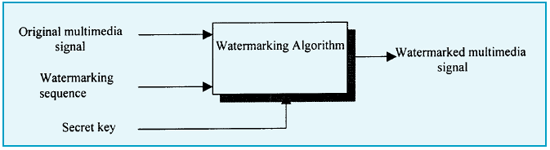
Fig 1 Watermark embedding process
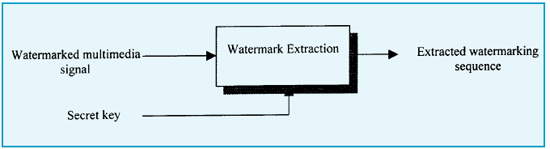
Fig 2 Watermark detection process
This is the mostbasic but non-trivial requirement that all watermarking schemes should meet. For most applications, the watermark should also be robust to some intentional/ unintentional attacks. To provide a robust watermark, a good strategy is to embed the watermark signal into the significant portion of the host signal. Visible watermarks, as the name says, are visual
patterns, like logos, which are inserted into or overlaid
on images (or video), very similar to visible paper
watermarks. Visible watermarks are mainly applied to
images, for example, to visibly mark preview images
available in image databases or on the World Wide Fragile watermarks do not survive lossy
transformations since their purpose is tamper detection
in the original signal. There are many effective ways
to insert a fragile watermark into digital content while
preserving the imperceptibility requirement [8]. Placing
the watermark information into the perceptually
insignificant portions of the data guarantees
imperceptibility and provides fragile marking For security applications and copyright protection, robust watermarking techniques have been proposed [9-12]. |
Here the technical challenge is to provide transparency and robustness that are conflicting requirements. Ideally, an effective, robust watermarking scheme provides a mark that can only be removed when the original content is destroyed as well. Spatial and Spectral Watermark The watermark in a signal can be embedded in the
spatial domain [13] or in transform domain like the
discrete cosine transform (DCT) domain, discrete
Fourier transform (DFT) or wavelet domain [14-16].
For image watermarking the signal embedding is done
by signal-adaptive (i.e. scaled) addition, mostly to the
luminance channel alone, but sometimes color channels
are also included. It is often claimed that embedding
in the transform (mostly DCT or wavelet) domain is
advantageous in terms of visibility and security.
However, while some authors argue that the watermarks
should be embedded into low frequencies, others argue
that they should rather be embedded into the medium
or high frequencies. In fact, it has been shown that for
maximum robustness, signal adaptive watermarks
should be embedded into the same spectral components |